Published: August 2025
Author: TheCyberGuyAU
Overview
North Korean cyber actors have significantly escalated their tactics in 2025. From using legitimate platforms like GitHub for espionage to infiltrating hundreds of global companies through fake remote IT workers, the threat landscape is evolving rapidly.
This post breaks down the two major campaigns that every security-conscious business should understand.
Campaign 1: GitHub Used in Diplomatic Cyber Attacks
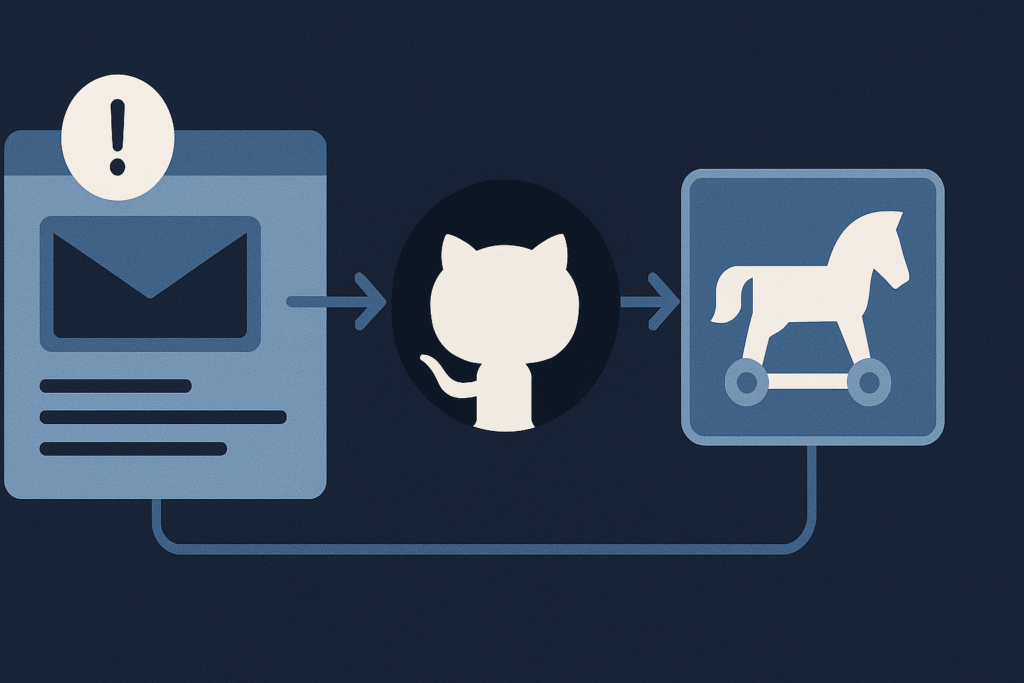
Between March and July 2025, multiple diplomatic missions in South Korea were targeted by spear-phishing campaigns.
Key Tactics:
- Attackers impersonated diplomats and officials, sending emails in multiple languages with meeting invites or event documents.
- Payloads were delivered via Dropbox, Google Drive, and Korean cloud services.
- A malicious Windows LNK file executed PowerShell scripts.
- GitHub repositories were used as command-and-control (C2) channels.
- Decoy documents were used to maintain cover during compromise.
Objective:
To install variants of the Xeno RAT (also known as MoonPeak) and collect system data, credentials, and access to diplomatic systems.
Campaign 2: Fake Remote Workers Infiltrating Global Firms
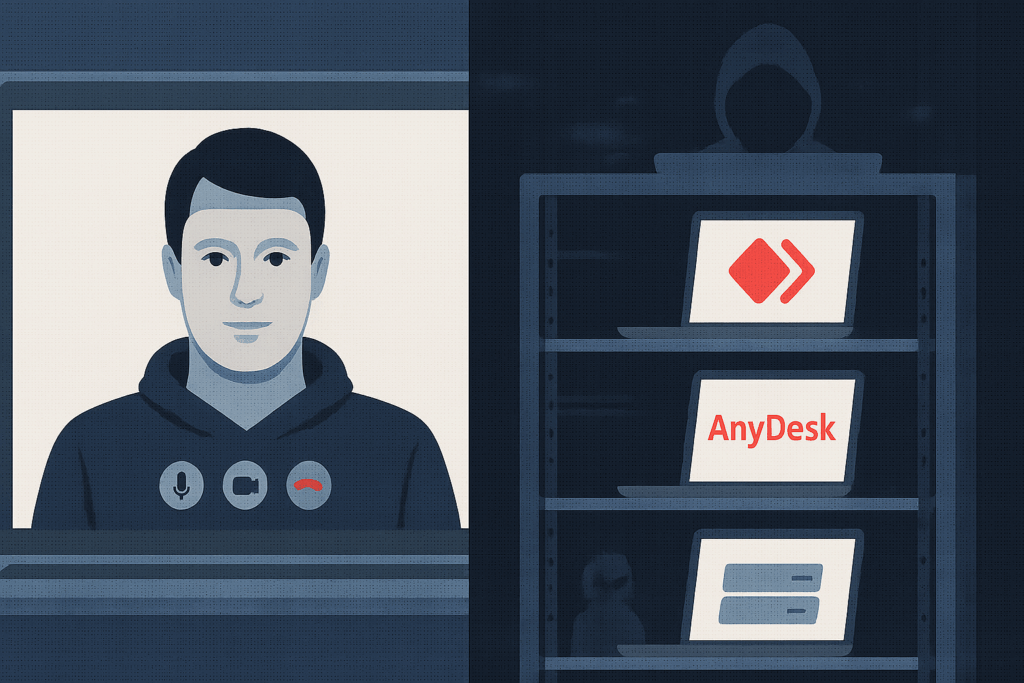
A separate but equally concerning operation involved North Korean operatives posing as remote IT workers.
Notable Findings (via CrowdStrike and others):
- Over 320 companies were unknowingly infiltrated.
- Operatives used generative AI to write code, draft résumés, and respond to messages.
- Some applicants used real-time deepfakes during video interviews.
- Access was maintained via tools like AnyDesk and VPNs.
- Disposable email addresses and privacy tools (like ProtonMail) were widely used.
- Many of these operatives were working multiple jobs simultaneously.
Implications for Australian Businesses
Whether you’re hiring remote freelancers, using AI development tools, or working with international vendors, these risks are real and growing.
Core Business Risks:
- Insider threats from unknown contractors
- Supply chain and codebase compromise via GitHub or open-source tools
- Regulatory exposure due to mishandling of sensitive data
Recommendations
- Implement strict remote identity verification.
Don’t rely on résumés and LinkedIn profiles alone. - Define AI use and code tool access in your security policies.
- Monitor unusual cloud platform activity.
Especially platforms like GitHub, Dropbox, and Google Drive. - Train hiring teams and IT staff on these tactics.
- Deploy endpoint detection and insider threat monitoring.
Final Thoughts
Cyber warfare today isn’t limited to ransomware or malware — it’s about persistence, infiltration, and trust manipulation.
North Korea’s campaigns are a wake-up call. It’s time for Australian businesses to get serious about remote work verification, GitHub security, and AI use policy enforcement.
Coming Soon
A new free resource:
“Remote Work & AI Security Risk Assessment Checklist”
Optimised for SMEs and IT managers.
Written by:
Ateeq Sheikh — TheCyberGuyAU
Helping Aussie businesses protect data, assets, and trust.