Introduction: The Perimeter Didn’t Disappear — It Moved
For decades, cybersecurity strategy revolved around one assumption: if you could protect the network, you could protect the business.
Firewalls were strengthened.
VPNs were expanded.
Perimeters were hardened.
That approach made sense when:
- Applications lived on-prem
- Users worked from offices
- Networks defined trust boundaries
But that world no longer exists.
In 2026, organisations operate in a reality where:
- Applications are SaaS-based
- Data is distributed across cloud platforms
- Users authenticate directly to services
- Networks are no longer the control plane
Attackers haven’t adapted by becoming more technical. They’ve adapted by becoming more patient.
They steal credentials.
They reuse access.
They wait.
And that’s why identity has become the most important control point in modern cybersecurity.
The Shift: From Network Security to Identity Security
The most common misconception in cyber today is that identity is just another layer in the stack.
It isn’t.
Identity has replaced the network as the primary decision-making surface for access. Industry analysis confirms that identity-based security is now the cornerstone of Zero Trust architectures, with authentication decisions happening at the service level rather than network perimeter [Source].
Every meaningful security decision now starts with:
- Who is this user?
- What are they trying to access?
- Under what conditions?
If identity controls are weak, everything downstream inherits that weakness.
The Data Confirms It: Breaches Are Identity-Driven
Recent breach analysis consistently shows the same pattern—and the numbers are sobering:
Credential theft surged 160% in 2025, with 1.8 billion credentials compromised in just the first six months of the year [Source].
78% of data breaches now involve unauthorized access—meaning attackers are logging in with valid credentials rather than exploiting technical vulnerabilities [Source].
Credential-based attacks now account for 20% of all breaches globally, representing the fastest-growing attack vector in enterprise environments [Source].
This matters because:
- Logging in looks legitimate
- Alerts trigger later — if at all
- Detection and response take longer
The result isn’t just more breaches—it’s worse breaches. When attackers use valid credentials, they move laterally with impunity, often remaining undetected for months.
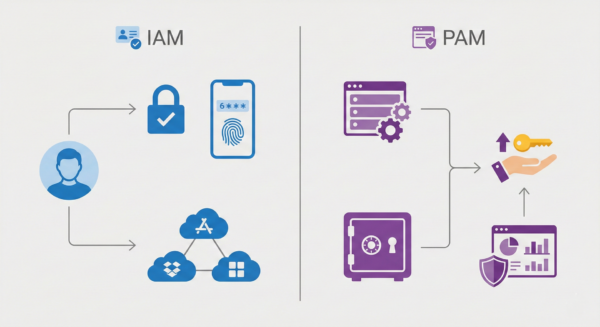
Understanding IAM: Access Control at Scale
Identity and Access Management (IAM) is responsible for governing:
- Authentication
- Authorization
- Identity lifecycle
At scale, IAM ensures that:
- Users get access quickly
- Access aligns to role and context
- Access is removed when no longer needed
Core IAM components typically include:
- Single Sign-On (SSO) – Centralized authentication across applications
- Multi-Factor Authentication (MFA) – Verification beyond passwords
- Conditional access – Context-aware authorization based on risk signals
- Identity governance – Lifecycle management for joiners, movers, and leavers
IAM answers the fundamental question: “Should this person be allowed in—right now?”
IAM is foundational—but it is not sufficient on its own.
Understanding PAM: Containing Privilege and Risk
Privileged Access Management (PAM) exists to manage the most dangerous identities in any environment.
Privileged identities can:
- Change system configurations
- Access sensitive data repositories
- Bypass normal security controls
- Execute commands at infrastructure level
Without PAM:
- Privilege becomes permanent
- Service accounts go unmonitored
- Abuse becomes invisible
- Lateral movement accelerates
Modern PAM focuses on:
- Just-in-time (JIT) access – Temporary privilege elevation only when needed
- Credential vaulting – Secure storage and automated rotation of privileged credentials
- Auditable sessions – Recording and monitoring of privileged activities
- Least privilege enforcement – Limiting access to the minimum required
PAM answers the critical question: “Once inside, how much damage could this identity do?”
PAM doesn’t slow the business down. It stops small failures from becoming catastrophic ones.
Why IAM Without PAM Fails in Practice
Many organisations stop at IAM and believe the job is done. “We’ve deployed MFA—we’re secure.”
This creates critical blind spots:
- Admin accounts with standing access – Permanent elevation that never expires
- Third-party elevated permissions – Vendor access that persists beyond project completion
- Service accounts that never rotate – Automated credentials unchanged for years
- Shadow admin privileges – Elevated access hidden in application layers
These identities become ideal targets. The average window for exploitation after credential exposure is 94 days [Source]—yet many privileged accounts remain static for far longer.
Attackers don’t need persistence exploits when privilege already exists and is never removed.
Identity Sprawl: The Hidden Risk Multiplier
As environments grow and digital transformation accelerates, identity sprawl becomes inevitable:
- Identities multiply across platforms
- Access accumulates with each role change
- Visibility decreases as complexity grows
Without active governance:
- Old permissions linger after employees leave or change roles
- Privilege expands silently through exception requests
- Accountability disappears when ownership is unclear
- Service accounts proliferate without central tracking
Industry standards mandate credential rotation every 30-90 days for privileged accounts (PCI DSS, NIST, ISO 27001) [Source], yet compliance often lags reality.
This is how breaches escalate quietly—and why detection often comes too late. By the time anomalous behavior triggers alerts, attackers have already achieved their objectives.
Zero Trust Starts (and Fails) With Identity
Zero Trust is frequently misunderstood as a product or architecture you can purchase.
In reality, it’s a discipline—a set of principles that must be built into operations.
And identity is its foundation [Source].
Zero Trust requires three pillars:
- Strong authentication (IAM) – Verify every identity, every time
- Least privilege (PAM) – Grant minimal access, time-bound when possible
- Continuous validation – Monitor behavior and context constantly
Without IAM and PAM working together:
- Authentication becomes meaningless if privilege isn’t controlled
- Monitoring can’t detect abuse if access is too broad
- Incident response is reactive rather than preventive
Zero Trust isn’t about distrust—it’s about verification at every step. IAM and PAM make that verification possible and enforceable.
Service Accounts: The Most Overlooked Attack Vector
Service accounts represent one of the highest-impact gaps in most IAM/PAM programs.
Why service accounts are dangerous:
- They often have elevated privileges across multiple systems
- They rarely rotate credentials, sometimes running for years unchanged
- They typically bypass MFA entirely for operational convenience
- They sit outside normal identity governance, with unclear ownership
- They’re hard to monitor—distinguishing normal vs. malicious activity is difficult
Attackers specifically target service accounts because they provide:
- Persistent access that doesn’t expire
- High privilege without requiring social engineering
- Low detection risk due to expected automation patterns
Effective service account management requires:
- Automated credential rotation (aligned to compliance windows)
- Clear ownership and accountability
- Privilege scoping to specific functions
- Behavioral monitoring for anomalies
The Australian Context: Regulation, Insurance, and Reality
Australian regulators are increasingly explicit about identity as a risk control surface:
OAIC’s Digital ID Regulatory Strategy focuses explicitly on safe identity verification practices and data handling for digital identity systems [Source].
Cyber insurance underwriters now routinely assess:
- MFA coverage across all access points
- Privileged access governance and monitoring
- Identity lifecycle management maturity
- Incident response capability around credential compromise
Regulatory expectations have shifted from reactive breach notification to proactive risk management. Regulators now ask:
- Were your controls reasonable given known threats?
- Could you evidence governance over privileged access?
- Did you monitor and respond to access anomalies?
Boards are no longer comfortable with: “IT has it covered.”
They want evidence. IAM and PAM provide it—through audit trails, access reviews, and governance reporting.
A Practical, Executable Starting Point
You don’t need perfection. You need progress.
If you’re early in your IAM/PAM journey, start here:
1. Enforce MFA Everywhere
No exceptions. This includes:
- Admin consoles
- VPN access
- Cloud platforms
- Remote access tools
2. Identify All Privileged Accounts
Map out:
- Human admin accounts
- Service accounts
- Third-party vendor access
- Emergency break-glass accounts
3. Remove Standing Privilege
Wherever possible:
- Implement just-in-time elevation
- Set time-bound access windows
- Require approval workflows for privilege requests
4. Implement Credential Rotation
Especially for:
- Service accounts
- Shared accounts (eliminate where possible)
- API keys and tokens
5. Review Access Regularly
Quarterly at minimum:
- Validate who still needs access
- Remove orphaned accounts
- Audit privilege creep
- Review third-party access
These steps reduce risk immediately—and provide tangible evidence of governance for regulators and insurers.
Common Mistakes That Undermine IAM/PAM Programs
Treating PAM as a Project, Not a Program
PAM isn’t implemented once and forgotten. It requires:
- Ongoing access reviews
- Continuous privilege discovery
- Policy refinement as environments change
Over-Reliance on Technology Without Governance
Tools don’t solve organizational problems. Effective IAM/PAM requires:
- Clear ownership and accountability
- Business involvement in access decisions
- Integration with HR and change management processes
Ignoring Identity Lifecycle
Access must be tied to employment lifecycle:
- Automated provisioning for joiners
- Role-based adjustments for movers
- Immediate deprovisioning for leavers
No Visibility Into Service Account Usage
Without monitoring:
- You can’t distinguish normal vs. abnormal behavior
- Compromise remains undetected
- Forensics become impossible post-incident
Final Takeaway: Identity Is the Deciding Factor
Cybersecurity outcomes in 2026 are determined less by tools—and more by control.
Identity determines:
- How breaches start – Through stolen or compromised credentials
- How far they spread – Based on privilege and lateral movement capability
- How regulators respond – Whether controls were reasonable and evidenced
If identity is weak, everything else is exposed. Your encryption, your EDR, your SIEM—all become irrelevant if an attacker logs in with valid credentials.
Identity is the real perimeter.
The question isn’t whether to invest in IAM and PAM. It’s whether you can afford not to.
Next Steps
If your organisation is investing in cyber but still unsure whether risk is actually being reduced, it’s time to look at identity properly.
I work with Australian organisations to design IAM and PAM strategies that are:
- Practical – Aligned to business operations, not just compliance checkboxes
- Defensible – Evidenced through audit trails and governance reporting
- Risk-focused – Addressing real attack patterns, not theoretical threats
👉 Visit thecyberguyau.com
👉 Or DM me on LinkedIn
About the Author: I help Australian organisations move from identity chaos to controlled, auditable access that reduces real cyber risk. This means practical IAM and PAM strategies that boards can understand and regulators can accept.